Many APIs require that the calling application provide identity information to the API service. Usually, you would expect the API Key to provide the identifying information, but we are not quite there yet. For the time being, when an API requires that the calling application send over identifying information a secondary header is added to the request with a Campus LDAP username and password combination. These Campus LDAP username/password combinations will identify the application. They will not be your personal ucsbNetId and password. There are two types of Campus LDAP Identities that can be sent: Application or Functional.
Useful Resources
Campus LDAP Application Accounts
This is the preferred account type to be used. These accounts are stored in the Campus LDAP ou=Applications. That is a designation which helps campus determine that account represents an system rather than a human being (ou=People).
Requesting an LDAP Service Account
To request a Campus LDAP Service Account:
- Log into https://etsc.ucsb.edu.
- Click on Advanced Technical Services > Identity and Access
- Click on Create UCSBNetID Functional Account
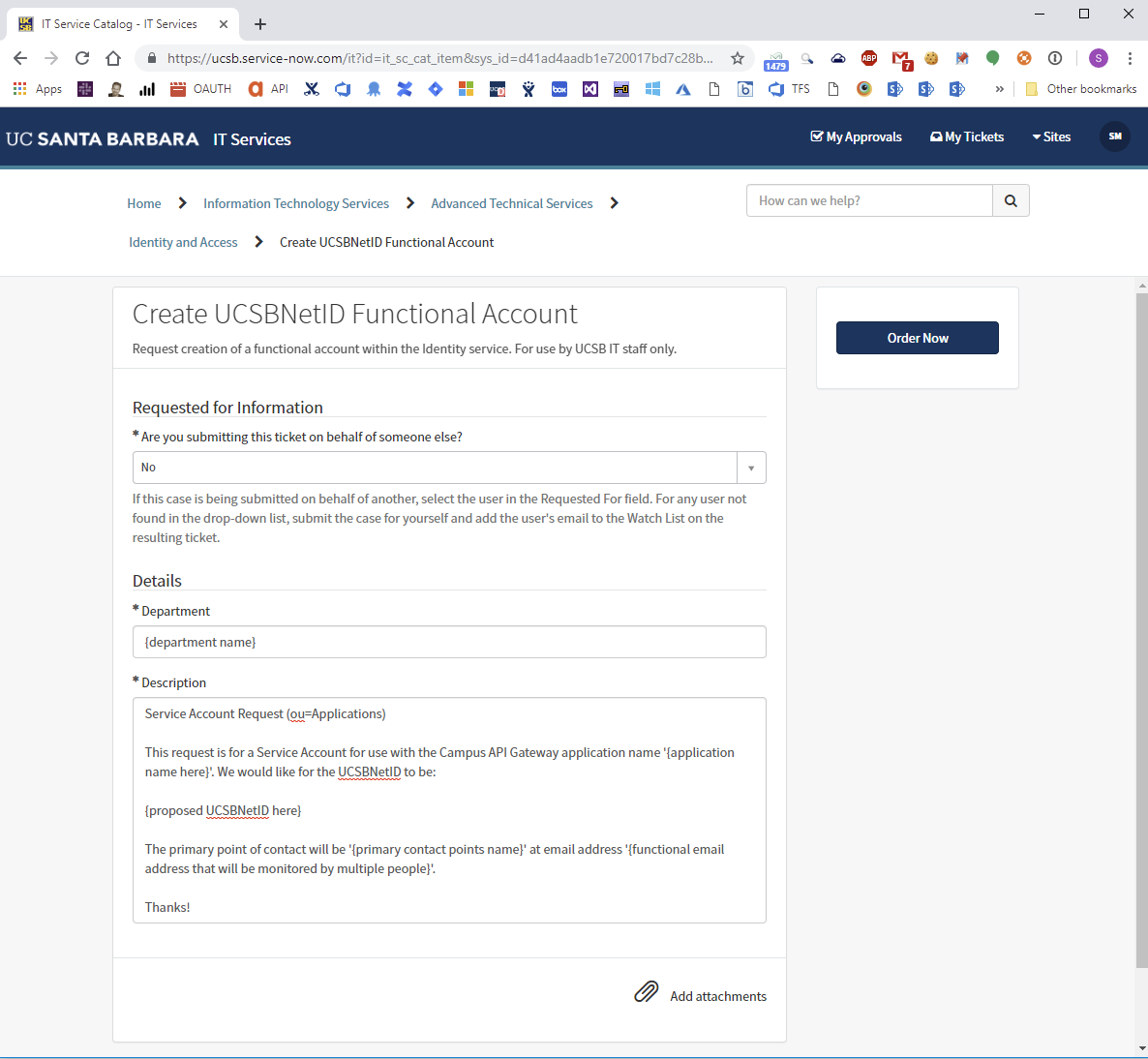
- Then fill out Department and Description with:
Application Account Request (ou=Applications)
This request is for a Application Account for use with the Campus API Gateway application name '{application name here}'. We would like for the UCSBNetID to be:
{proposed UCSBNetID here}
The primary point of contact will be '{primary contact points name}' at email address '{functional email address that will be monitored by multiple people}'.
Thanks!
Functional Accounts
Functional Accounts are stored in the Campus LDAP under ou=People. This is not the designation that the campus would like for accounts that represents applications. However, Functional Accounts do have more limited functionality than Application Account do and because of that they are preferred when working in an environment that could have a greater chance of exposure. For example, a mobile application that ran on a cell phone would pose a greater security risk, so a more limited Functional Account would be used.
Requesting an LDAP Functional Account
To request a Campus LDAP Functional Account:
- Log into https://etsc.ucsb.edu.
- Click on Advanced Technical Services > Identity and Access

- Click on Create UCSBNetID Functional Account

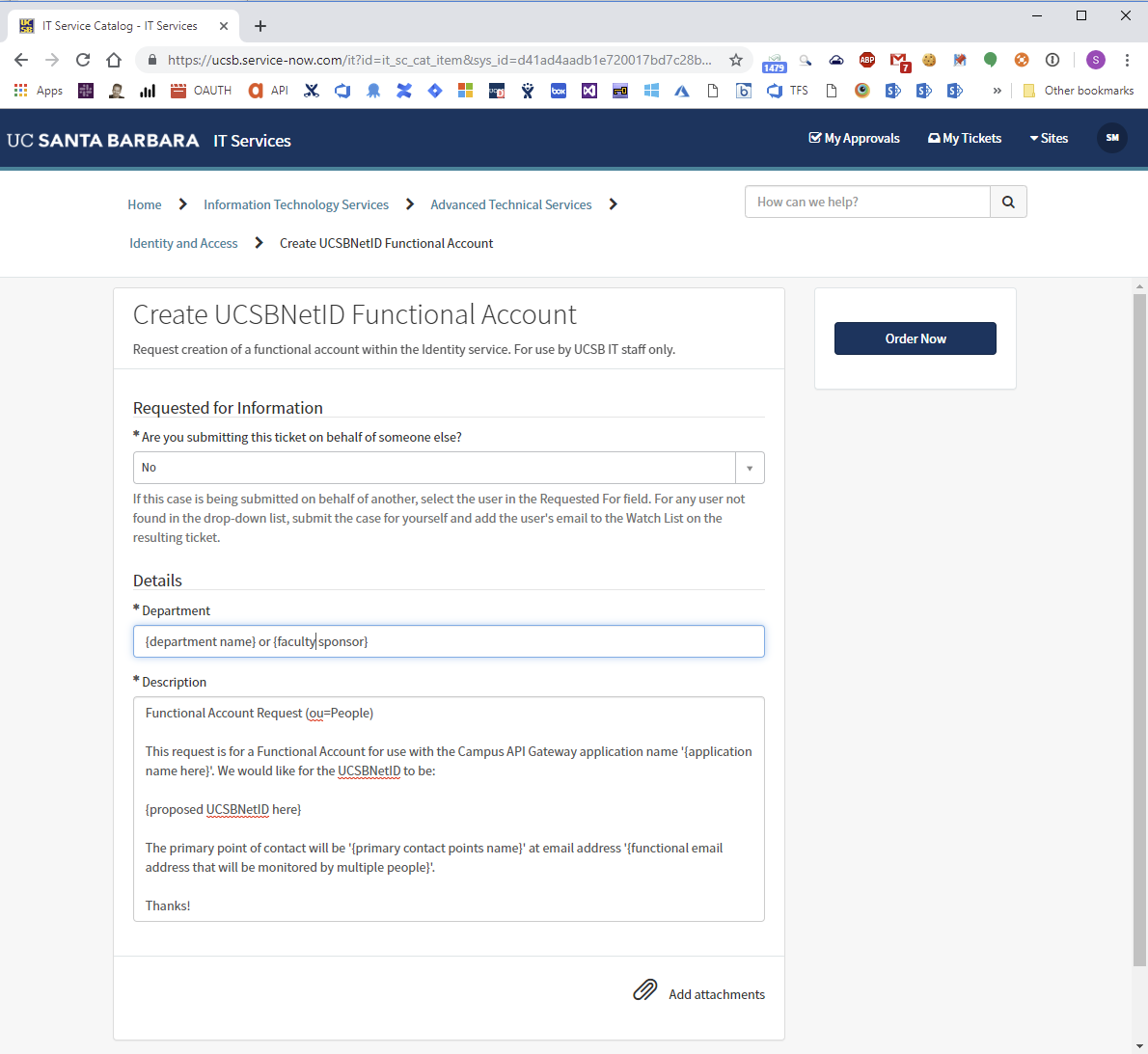
- Then fill out Department and Description with:
Functional Account Request (ou=People)
This request is for a Functional Account for use with the Campus API Gateway application name '{application name here}'. We would like for the UCSBNetID to be:
{proposed UCSBNetID here}
The primary point of contact will be '{primary contact points name}' at email address '{functional email address that will be monitored by multiple people}'.
Thanks!
Accounts for Student Applications
Application accounts have an extra set of privileges which allow them to read information from the Campus LDAP (beyond the public information). Because of these extra privileges, Student developed applications fit the Functional Account designation a little bit better. In order for a Student application to get a Campus LDAP Functional, the application should be sponsored by a Faculty member (or Department Staff) and include information in their request about who the sponsor is and how to contact them for confirmation.
